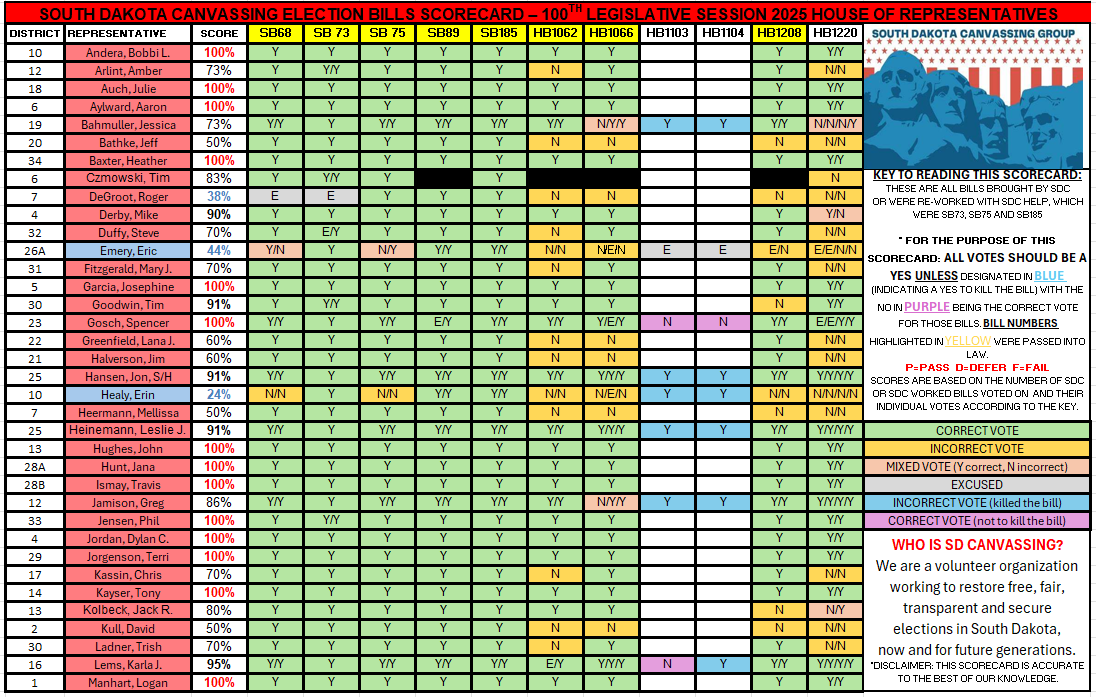
SB217 failed by one vote in Senate State Affairs after a very limited time of public testimony. Systems expert, Clay Parikh, was online as an expert witness, but was given virtually no time to properly convey the serious security issues with the machines.
What you didn’t get to see were the four national subject matter experts that wrote in urging the South Dakota State Legislature to ban the machines in an effort to protect the electorate, the constitution, and national critical infrastructure.
Col. Shawn Smith – Ret., Air Force
An excerpt from the Declaration of Shawn Smith filed in the Circuit Court of Montgomery County, Alabama.
1. My name is Shawn A. Smith. I am a retired military officer. I have Master’s degrees in National Security Affairs from the Naval Postgraduate School and in Aeronautical Science from Embry-Riddle Aeronautical University. I have held an active Top Secret security clearance since 1992 and have been cleared for Sensitive Compartmented Information since 1996.
2. My military occupational specialty was space and missile operations, and I have extensive experience over 25+ years of active duty service in operating, specifying requirements for, planning the procurement of, training, testing, and commanding the employment of complex, computer-based military weapon systems.
3. My military service included significant experience in Special Technical Operations, involving advanced technology, at every level from tactical employment through operational planning, national-level policy, Presidential tasking, and requirements definition and procurement of future sensitive capabilities. I have conceived, and advised agencies within the United States Government on, opportunities and technical approaches for supply chain compromise to affect foreign adversaries’ ability to wage war against the United States, and to benefit United States national security.
4. My final active duty assignment prior to retirement in 2017 was for four years as the Senior Military Evaluator for Space and Intelligence, Surveillance, and Reconnaissance systems in the office of the Director, Operational Test & Evaluation, under the Office of the Secretary of Defense. In that role, I was responsible to execute the Director’s oversight of operational testing of all non-satellite communications space systems in the Department of Defense, including the Global Positioning System, the Space-Based Infrared System, the Space Fence, the Geosynchronous Space Situational Awareness Program, and many others. Execution of that oversight required subject matter expertise in the space domain, in the technologies involved in each system, in Scientific Test and Analysis Techniques to determine adequate and efficient test designs, and in the threat capabilities and modus operandi of foreign nation states, with respect to U.S. national security.
5. After retirement, I continued to support the Director, Operational Test & Evaluation as a consultant to adversarial assessment project teams which reviewed the results of cyber threat conduct against U.S. governmental and non-governmental national security targets by foreign adversaries, drew conclusions about the risks and impacts of that conduct, and wrote recommendations for responsive and preventive changes in technology, force structure, and defense policy, which the Director provided under his signature to the heads of the military Departments, the Secretary of Defense, and the President of the United States.
6. I have been asked to testify about the threat of supply chain compromise and attack to U.S. national security systems and critical infrastructure, in particular to election-related systems, including voting systems and, consequently, to elections. This declaration will define and describe supply chain compromise threats, provide examples, explain that they have become pervasive and sophisticated, affecting and placing at risk the supply chain for U.S. computer systems and components, and explain the consequent ramifications for and vulnerability of U.S. election and voting systems. The information presented is unclassified and based upon my personal experiences, publicly available reporting, studies, events, incidents, policy, and de-classified U.S. Government information.
7. Given my background, experience, education, and training, and now my exposure to and understanding of the technology employed in U.S. election systems, my conclusion is that U.S. elections are critically vulnerable to exploitation by foreign adversaries through supply chain compromise of our computerized election systems.

Dr. Walter Daugherity –
Computer consultant and also Senior Lecturer Emeritus in the Department of Computer Science and Engineering at Texas A&M University. He graduated from Oklahoma Christian University with a degree in mathematics, and then earned master’s and doctor’s degrees from Harvard University, which he attended on a Prize Fellowship from the National Science Foundation. (Resume below)



David Clements –
Is an attorney, and former award-winning business law professor and prosecutor. During his legal career, Professor Clements was a leader in trial teams that secured eight first degree murder convictions, including members of the “AZ Boys” drug trafficking organization.
Professor Clements now applies his vast evidentiary and courtroom experience to the realm of elections. His advocacy has led to audits and canvassing operations being implemented across the country, with some efforts resulting in elimination of election machines that facilitate fraud.
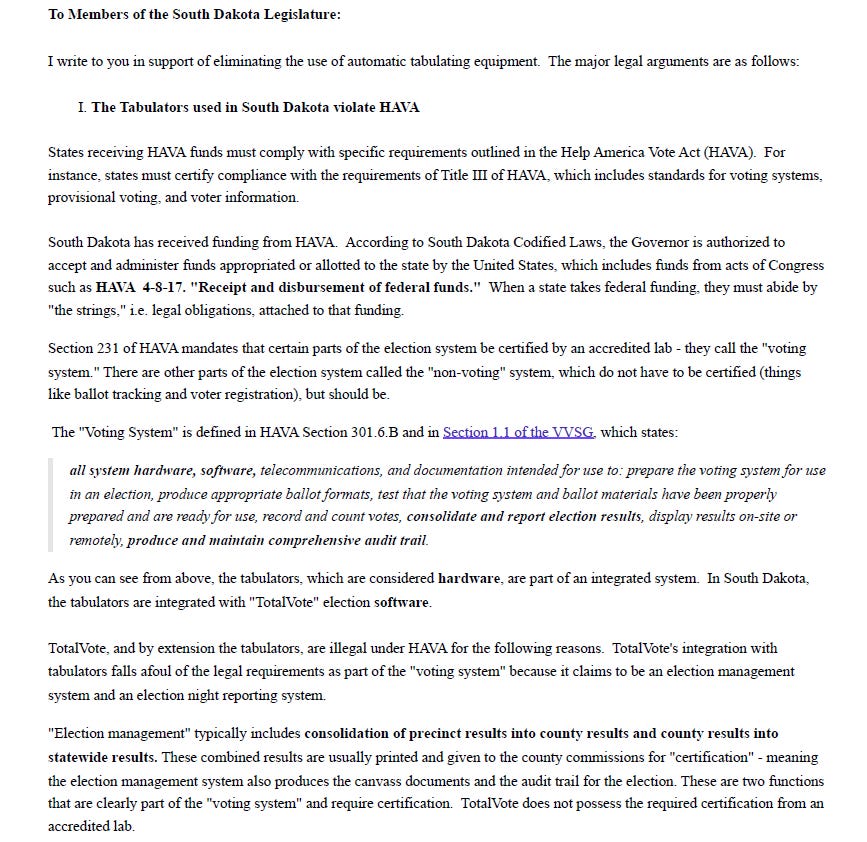
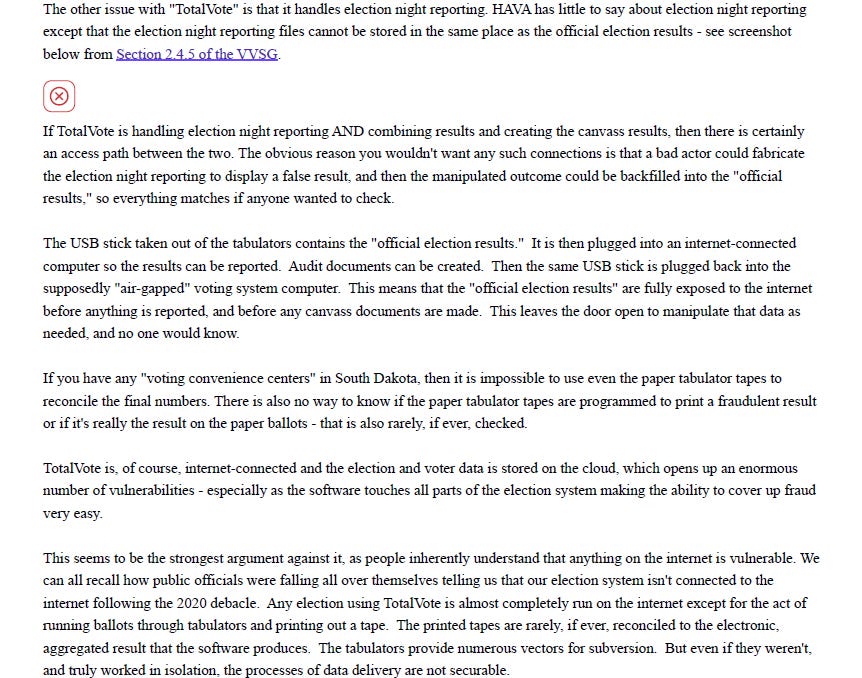


Clay Parikh –
An excerpt from the Declaration of Clay Parikh –
2. I have a Master of Science in Cyber Security, Computer Science from the University of Alabama in Huntsville. I have a Bachelor of Science in Computer Science, Systems Mc jor from the University of North Carolina at Wilmington. In February 2007 I obtained the Certified Information Systems Security Professional (CISSP) certification and have continually maintained good standing. I also hold the following certifications: Certified Ethical Hacker (CEH) and Certified Hacking Forensic Investigator (CHFI).
3. Since December 2003 I have continually worked in the areas of Information Assurance (IA), Information Security and Cyber Security. I have performed countless Root Cause Analyses (RCA) to determine the root causes of equipment malfunctions, system, and network issues. I also have a IT Infrastructure Library (ITIL)v3 certification, focused on a global framework of best practices for systematic risk management, customer relations, and delivery of stable, scalable, adaptable organizational IT environments.
4. From 2008 to 2017, I worked through a professional staffing company for several testing laboratories that tested electronic voting machines. These laboratories included Wyle Laboratories, which was later acquired by National Technical Systems (NTS), and Pro V&V. My duties were to perform security tests on vendor voting systems for certification of those systems by either the Election Assistance Commission (EAC), to Federal Voting System Standards (VSS) or Voluntary Voting System Guidelines (VVSG), or to a specific state’s Secretary of State’s requirements.

For some reason our legislators seem to think the auditors who can’t even VIEW the AUDIT TRAIL to their machines, much less know what to do with it, are the so-called “experts”; or the indoctrinated propaganda pushing stooges in the SOS office. They are only experts at absorbing and regurgitating the falsehoods they memorized in training sessions put on by corrupt election vendors and weaponized federal agencies like CISA or NGO’s such as the EI-ISAC and EIP.
The REAL EXPERTS, with the credentials to back it up, issue a dire warning here.
South Dakota lost another opportunity to do the right thing.
The choice to know has always been ours.